EMR HIPAA Compliance Checklist: Strategic Guide for CTOs
.avif)
Look, let's be honest here. You've probably seen dozens of HIPAA compliance checklists that read like boring regulatory documents. They tell you what to do but completely miss the why behind strategic compliance decisions.
Here's the thing: if you're a healthcare CTO dealing with PE backing, rapid scaling, or preparing for an exit, you need more than checkbox compliance. You need a framework that actually protects your business while positioning you for success.
Think about it this way. Would you rather explain to your board why you failed an audit, or why your strategic compliance approach just added significant value to your company's valuation?
Executive Summary: The Business Case for Strategic EMR HIPAA Compliance
Traditional compliance checklists fail spectacularly when auditors start digging deep. Why? Because they treat HIPAA like a one-time project instead of an ongoing business strategy.
We're not just talking about regulatory compliance for covered entities anymore. We're talking about business survival, competitive advantage, and measurable ROI on your compliance investments.
Strategic EMR HIPAA compliance delivers:
- Reduced insurance premiums (we're talking real money here)
- Streamlined vendor partnerships (no more awkward compliance conversations)
- Accelerated contract negotiations (customers trust you faster)
- Enhanced competitive positioning (compliance becomes a differentiator)
Organizations implementing risk-based frameworks report 40% faster audit completions and 25% lower overall compliance costs.
That's not just compliance. That's a competitive advantage.
The True Cost of HIPAA Breaches: By the Numbers
CTOs know a breach can be costly, but recent data shows healthcare breaches are in a league of their own. According to IBM's 2024 Cost of a Data Breach study, the healthcare industry suffered the highest average breach costs of any sector at $9.8 million per incident in 2024 (down from $10.93 million in 2023, but still the costliest sector).
The global average across industries was less than half that (~$4.45M), and even the financial sector averaged only $5.9M. Healthcare has topped the cost list every year since 2011.
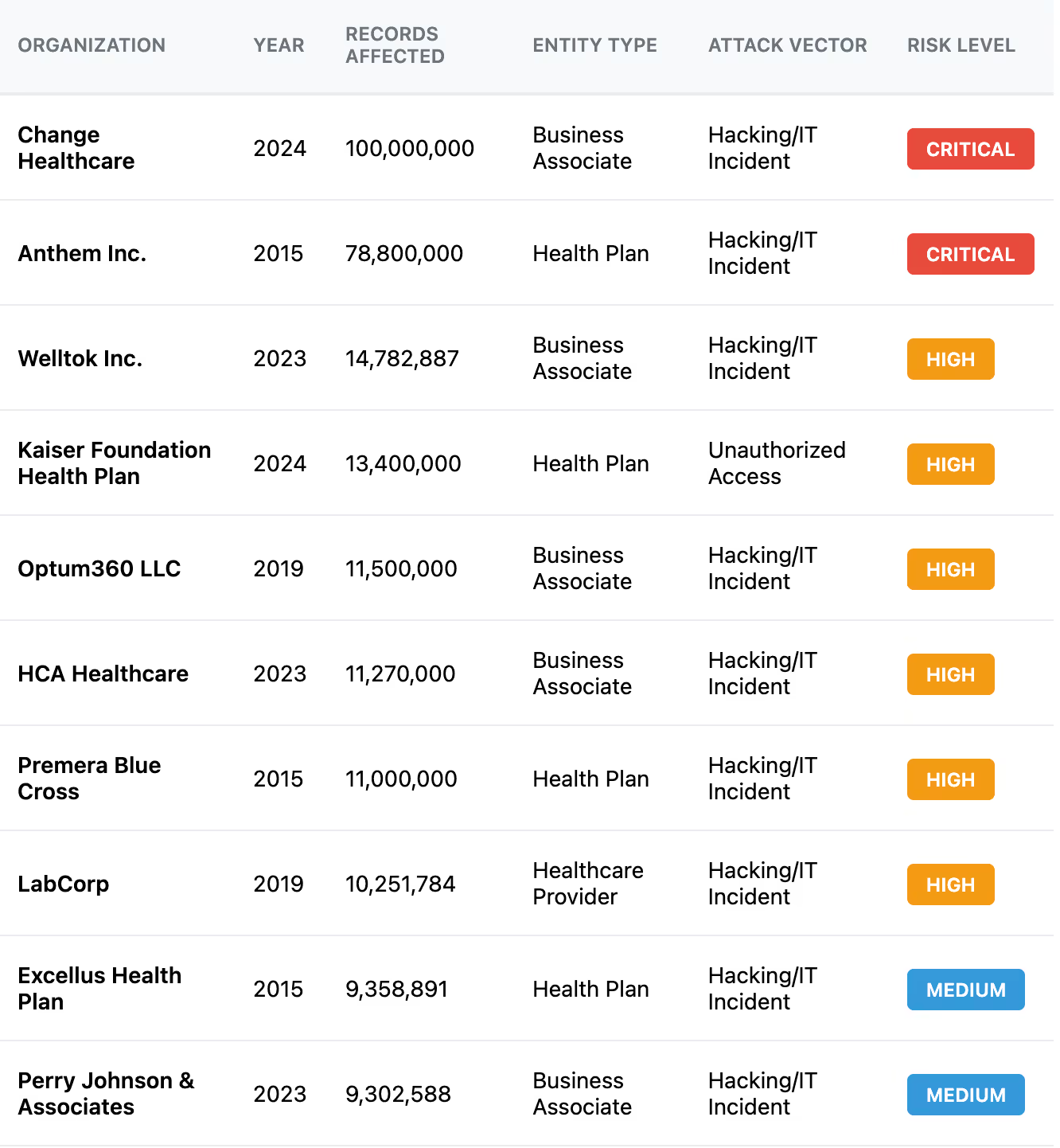
Why are healthcare breaches so expensive?
Beyond technical recovery, breach costs balloon from regulatory fines, legal settlements, patient notification, credit monitoring, and most of all lost business and trust. Studies find 70% of patients would consider switching providers after their data is compromised.
The Small Business Reality
Even without closure, reputational damage can haunt a healthcare company for years. One analysis of cyber insurance claims found that smaller healthcare providers had breach costs ranging from $1,000 up to $11 million, averaging around $103,000 per incident. Alarmingly, the average claim for these small providers jumped from ~$168k in 2020 to $541k in 2021.
But here's where it gets interesting. PE firms are now factoring compliance posture directly into valuations. Private equity experts warn that a serious cyber incident can tarnish the reputation of an entire portfolio company, directly diminishing its investment value.
Key Takeaway
Healthcare data breaches also take longer to detect and contain than other industries (213 days to discover on average), giving attackers ample time to wreak havoc. This high risk level underscores why proactive compliance and security investments are far cheaper than breach remediation.

Risk-Based HIPAA Compliance Framework for EMR Systems
Here's where most compliance programs go wrong: they follow regulatory sequence instead of business logic. Smart CTOs categorize requirements by actual business risk, not regulatory order.
Think of it like triaging patients in an ER. You don't treat people in the order they arrive. You treat the most critical cases first. Same principle applies to HIPAA compliance.
High-risk requirements are your "code red" situations. These create immediate threats to business continuity. We're talking direct patient data exposure, system access vulnerabilities, audit trail gaps. You've got 15 days max to handle these, or you're playing with fire.
Medium-risk requirements are your "urgent but stable" cases. They affect operational efficiency and audit readiness but won't sink your ship immediately. Give yourself 30 days to implement these properly.
Lower-risk requirements are your "routine care" items. Important for long-term health, but they won't kill you if they take 60 days to implement.
The secret sauce? Your implementation priority matrix should consider two factors: how often regulators scrutinize this requirement, and what happens if you mess it up. High scrutiny plus high impact equals immediate priority, regardless of how complex the implementation might be.
Want to know if your compliance investment makes sense? Calculate direct costs (technology, people, consultants) against risk mitigation value (reduced breach probability, faster audits, better vendor negotiations). Most organizations see positive ROI within 12 to 18 months when they implement strategic frameworks.
High-Risk Requirements (Immediate Priority)
Access Controls and User Authentication
This is your first line of defense, and honestly, it's where most breaches start. You need role-based access control (RBAC) that actually makes sense for how your people work. Multi-factor authentication isn't optional anymore. Implement it for all system access, period.
Here's what trips up most organizations: they forget about automated de-provisioning when employees leave. That former intern who quit six months ago? They probably still have system access. Implement privileged access management (PAM) for admin functions and establish clear access review procedures that actually happen.
Data Encryption - At Rest and In Transit
All patient health information needs AES-256 encryption when stored and TLS 1.2 minimum when moving around. This includes internal system communications. Don't assume your internal network is safe.
Cloud solutions must give you control over encryption keys. If your vendor controls the keys, you're basically trusting them with your entire compliance program. Would you hand over your house keys to a stranger?
Audit Logging and Monitoring
Every protected health information (PHI access) attempt, system modification, and security event needs to be logged. But here's the kicker. Those logs need to be immutable (can't be changed) and actually reviewed by humans.
Set up automated alerts for suspicious patterns such as:
- Multiple failed logins
- Unusual data access volumes
- After-hours system access
Most breaches have warning signs. You just need systems smart enough to catch them.
Business Associate Agreements (BAAs)
Every vendor that might even glimpse PHI needs a signed BAA before you flip the switch. No exceptions. This includes your cloud provider and your backup service, if they have access to workstations.
Keep all your BAAs in one place. Add to your client onboarding checklist a check on if you have a BAA with them.
Maintain a BAA tracking system and verify compliance regularly. Trust but verify. Your vendor's compliance is your compliance.
Medium-Risk Requirements (30-Day Implementation)
Employee Training and Access Management
Generic HIPAA training is worthless. Your training needs to be role-specific and include real scenarios your people actually face. A nurse needs different training than a system administrator. And document when you have employee training.
Implement regular access reviews. Quarterly is good, monthly is better for high-risk roles. Document every access decision because auditors will ask about them.
Incident Response Procedures
Murphy's law applies to healthcare IT: if something can go wrong, it will. Your incident response plan needs to be documented, tested, and updated regularly.
Items to add:
- Breach identification criteria (what constitutes an incident?)
- Notification timelines (you've got 60 days max for some notifications)
- Containment procedures
- Stakeholder communication protocols
Note: You may have a limited notification window based on your BAA
Run tabletop exercises quarterly. You don't want your first incident response to be during an actual incident.
Risk Assessment Documentation
This is the foundation everything else builds on. Conduct annual risk assessments that document specific risks to PHI and include mitigation strategies with realistic timelines.
Consider technology changes, regulatory updates, and business process modifications. Your risk assessment from two years ago is probably obsolete.
Physical Safeguards
This includes facility access controls, workstation restrictions, device controls, and secure disposal procedures. Implement clean desk policies and screen locks. It's basic, but it works.
For cloud-based organizations, your vendors handle most physical safeguards, but you still need to verify their compliance documentation.
Lower-Risk Requirements (60-Day Implementation)
Policy Documentation and Updates
Comprehensive policies create your governance framework. They need to be annually reviewed, accessible to relevant personnel, and include approval processes, version control, and employee acknowledgment procedures.
Contingency Planning
Business continuity during system disruptions requires data backup procedures, disaster recovery protocols, emergency mode operations, and regular testing. Maintain offsite backup capabilities and test recovery procedures regularly.
Compliance Monitoring Procedures
Ongoing assurance through regular security assessments, policy compliance reviews, and performance metrics tracking. Establish compliance reporting procedures and corrective action protocols.
Demystifying HIPAA Safeguards: Administrative, Physical, Technical
HIPAA's Security Rule is often boiled down to three safeguard categories, but what do those really entail for a CTO? Here's a breakdown of each, along with insight on which areas to prioritize and how to phase implementations.
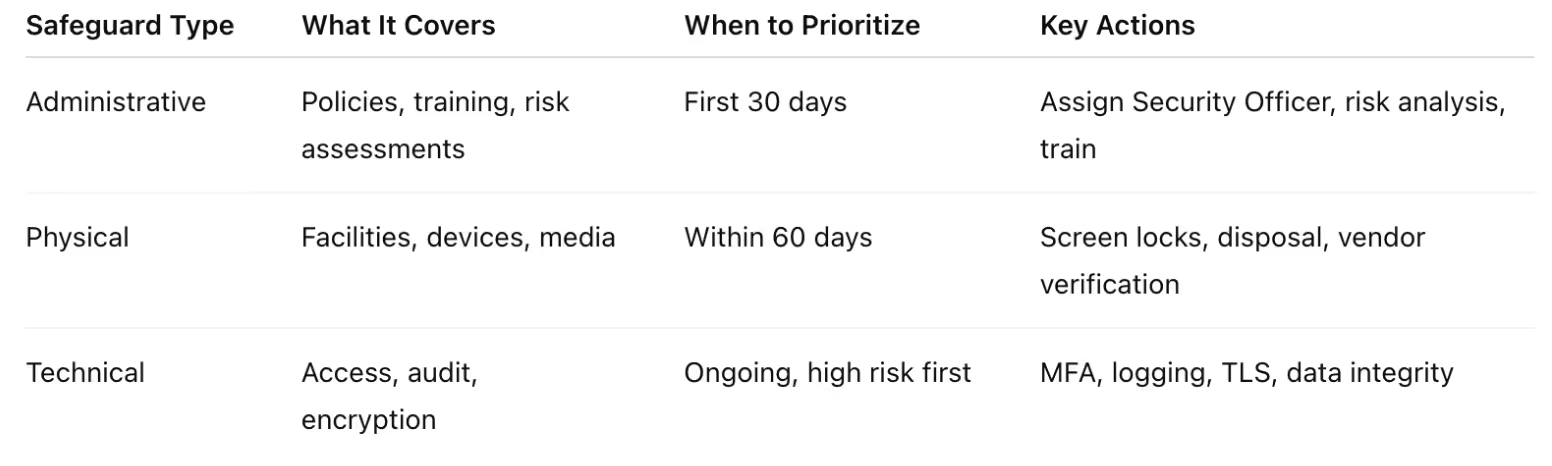
Administrative Safeguards: Your Foundation
These are the policies, procedures, and management processes that form your security foundation as required for covered entities under HIPAA.
Key requirements include:
- Conducting a risk analysis of ePHI vulnerabilities
- Appointing a security official
- Workforce access controls
- Security awareness training for employees
- Incident response procedures
- Contingency planning
- Periodic evaluations
In practice, a CTO should prioritize Administrative measures first. Performing a thorough risk assessment and addressing high-risk gaps early is not only required but also wise, since failing to identify obvious risks has led to some of the largest fines.
Within the first 30 days of a compliance initiative, you'll want to assign security responsibility, document initial policies, and kick off employee training on data handling. Administrative safeguards may not be flashy, but they set the stage for everything else.
Physical Safeguards: Quick Wins
These controls protect your facilities, hardware, and physical media containing PHI.
They include:
- Facility access controls (badge systems, locks, visitor procedures)
- Workstation security (positioning screens to prevent shoulder surfing, logging off idle sessions)
- Device/media controls for hardware containing PHI
Physical safeguards often present quick wins. Locking server rooms and using secure disposal of old hard drives are straightforward and high-impact. Implement these by the time you're storing any production data (within 60 days at latest).
Don't forget remote work considerations: even if using cloud infrastructure, employee laptops and home office practices fall under physical security. The good news is many physical protections are one-time setups or training points, but they must be consistently enforced.
Technical Safeguards: The Heavy Lifting
These are the technology measures that protect ePHI in systems and networks.
Key standards are:
- Access controls (unique user IDs, role-based access, automatic logoff, often now multi-factor authentication)
- Audit controls (logging user activity)
- Integrity controls (preventing improper alteration)
- Authentication (verifying identity)
- Transmission security (encrypting ePHI in transit)
Technical safeguards typically require the most ongoing effort and investment. A risk-based approach is crucial: address the most dangerous gaps first.
Encryption is a top priority.
Strong access management is another early win. Many breaches stem from compromised credentials, so cutting that risk is critical.
Aim to implement core technical controls in the first 60 days, then refine and harden them continuously.
The Strategic EMR HIPAA Compliance Checklist (45+ Requirements)
Let me walk you through the comprehensive checklist that actually works in the real world. This isn't just a regulatory exercise. It's your roadmap to bulletproof compliance.
Administrative Safeguards
Security Officer Assignment
With a small company, you need someone who owns this. Not as a side job, but as their primary responsibility. This person needs direct access to executive leadership and authority to implement security measures across your organization. Choose wisely. They're going to be your compliance quarterback. Someone in IT can do this if you give them the proper resources and budget.
At a larger company, you should have a chief security officer. You shouldn’t combine this with IT.
Workforce Training
Streamline your training and make sure everyone knows why it matters. Cover HIPAA requirements, your specific policies, and job-specific security procedures. Do this when people start, annually after that, and whenever you change significant policies.
Information Access Management
Create procedures for granting, modifying, and terminating access to PHI.
Include:
- Role-based controls
- Approval workflows
- Regular access reviews.
Document everything and automate it. Auditors love digital logs.
Security Awareness and Training
Develop ongoing programs addressing current threats and best practices.
Include:
- Phishing simulations (your people will hate them, but they work)
- Security bulletins
- Incident reporting procedures
Security Incident Procedures
Create plans covering identification, containment, investigation, and reporting.
Include:
- Notification procedures for patients
- Regulators
- Business partners
Test these procedures. Don't wait for a real incident to find out they don't work.
Contingency Plan
Develop business continuity plans ensuring continued PHI access during emergencies.
Include:
- Backup procedures
- Disaster recovery protocols
- Alternative processing capabilities
Periodic Security Evaluations
Conduct regular assessments of security effectiveness.
Include:
- Penetration testing
- Vulnerability assessments
- Policy compliance reviews
Schedule these like you would any other critical business activity.
Physical Safeguards
Physical safeguards vary dramatically depending on whether you manage your own infrastructure or use cloud services. Cloud providers like Microsoft Azure, AWS, and Google Cloud Platform document their physical safeguard compliance extensively, but you're still responsible for proper configuration and access management.
Facility Access Controls
Implement procedures controlling physical access to facilities containing PHI.
Include:
- Visitor management
- Access badges
- Monitoring for high-security areas
Workstation Use
Establish policies for workstation access and use.
Include:
- Screen locks
- Clean desk policies
- Restrictions on personal devices for PHI access
Device and Media Controls
Implement procedures for managing devices and media containing PHI.
Include:
- Asset tracking
- Secure disposal
- Controls for device movement
Technical Safeguards
Access Control
Implement technical policies controlling PHI access.
Include:
- Unique user identification
- Emergency access procedures
- Automatic logoff
- Encryption capabilities
Audit Controls
Deploy systems recording activity in information systems containing PHI.
Include:
- Comprehensive logging
- Analysis procedures
- Automated monitoring
Integrity
Implement security measures ensuring PHI integrity and protecting against unauthorized changes.
Include:
- Checksums
- Digital signatures
- Version control
Person or Entity Authentication
Verify user identity before allowing PHI access.
Implement:
- Multi-factor authentication
- Strong password requirements
- Regular authentication system reviews
Transmission Security
Protect PHI transmitted over networks.
Implement:
- Encryption for all transmissions
- Secure communication protocols
- Network segmentation for PHI systems
Organizational Requirements
Business Associate Contracts
Execute compliant BAAs with all vendors, contractors, and partners who may access PHI. Include specific security requirements, incident notification procedures, and audit rights.
Cloud Compliance Tools: AWS, Azure, and Google Cloud
If your custom-built EMR or digital health app is in the cloud, leveraging your cloud provider's compliance offerings can save enormous effort. The big three all provide HIPAA-aligned tools, templates, and governance frameworks, but you need to know how to use them.
Amazon Web Services (AWS)
AWS will sign a HIPAA Business Associate Addendum (BAA) with customers, covering over 130 AWS services that are "HIPAA Eligible" for PHI workloads. This includes all the core services (EC2, S3, RDS, etc.) and many advanced ones.
Key AWS Tools for HIPAA Compliance:
- AWS Config's conformance packs provide sample compliance rule sets mapping to HIPAA standards
- Operational Best Practices for HIPAA offer pre-built CloudFormation templates so your infrastructure meets HIPAA requirements by default
- AWS Security Hub and CloudWatch implement "Compliance as Code" for continuous monitoring
- AWS Audit Manager HIPAA framework auto-generates evidence of controls for audits
The documentation is extensive, but it's worth reading. Your compliance depends on proper configuration.
Remember:
AWS handles physical data center security and underlying infrastructure, while you must configure the cloud services securely. Don't forget to actually accept the AWS BAA via the AWS Artifact portal (it's not automatic).
Microsoft Azure
Microsoft's enterprise cloud comes with HIPAA compliance baked into many services by default. Healthcare organizations can further leverage Microsoft Azure for specialized medical data processing and document handling while maintaining these compliance standards.
Microsoft will sign a BAA that covers all in-scope Azure services. In fact, the Microsoft Product Terms include a HIPAA BAA covering Azure, Office 365, Dynamics, and other cloud services by default for healthcare customers.
Azure's HIPAA Advantages:
- Azure Policy Regulatory Compliance built-in initiative for HIPAA maps each Security Rule safeguard to specific Azure Policy controls
- HIPAA/HITRUST compliance baseline can be applied to your subscriptions for continuous assessment
- Blueprint for Healthcare deploys VMs, networking, Key Vault, logging in a compliant configuration
- Compliance Manager tracks HIPAA control implementation and generates audit-ready reports
Azure's strength is tight integration. If you're already a Microsoft shop (Office 365, etc.), you get a single BAA and consistent controls across your cloud and productivity tools.
Google Cloud Platform (GCP)
Google Cloud will also enter into a HIPAA BAA for covered services. You need to sign it (usually by request or via the Cloud console) to designate your projects as HIPAA accounts.
Notable GCP Features for Compliance:
- Cloud Data Loss Prevention (DLP) APIs that can detect and mask PHI in your datasets
- Cloud Healthcare API provides FHIR, HL7v2, and DICOM data processing with built-in compliance features
- VPC Service Controls create a security perimeter around healthcare data to mitigate exfiltration risks
- HIPAA Configuration Workbook lists each GCP service and how to configure it for HIPAA
GCP's turnkey approach reduces implementation complexity but may limit customization options compared to DIY solutions. Choose based on your team's technical capabilities and customization needs.
Multi-Cloud and Hybrid Considerations
Many healthcare organizations use a combination of on-premises, AWS/Azure/GCP, and even SaaS providers. Be aware that complex, multi-environment setups carry higher breach risks. IBM found breaches involving data spread across multiple clouds/on-prem had significantly higher costs and longer containment times.
Vendor Evaluation Criteria: BAAs, Red Flags, and Due Diligence
Here's something every healthcare CTO learns the hard way: all vendors will claim they're "HIPAA compliant," but that doesn't mean they actually are. And here's the kicker. They'll charge you more because they know you have to be compliant.
Selecting vendors and partners is a make-or-break area for HIPAA compliance. Under HIPAA, covered entities must ensure any service provider that handles PHI on your behalf must sign a Business Associate Agreement (BAA).
But a signed BAA is not a magic shield.
Verify BAA Coverage and Terms
First, ensure the vendor will sign a BAA and that all services you plan to use are included. A proper BAA should clearly define the vendor's obligations for safeguarding PHI and reporting any incidents.
Red flag: a BAA that lacks a breach notification clause or one that disclaims liability for data incidents. HHS sample BAA language requires reporting breaches to you without unreasonable delay and allows you to terminate the agreement if the BAA is in material breach.
Also ensure the BAA covers subcontractors. It should obligate the vendor to flow HIPAA requirements down to any subcontractors they use.
Security Program and Certifications
As part of due diligence, ask vendors for evidence of their security controls. Do they follow a framework like HITRUST or NIST? Many reputable BAAs undergo third-party audits (SOC 2 Type II reports, ISO 27001 certification, or HITRUST CSF certification).
Red flag: the vendor has no independent security assessments and simply says "trust us, we're HIPAA-ready." Regulators have penalized companies for relying on a vendor's word without verification.
Security Due Diligence Checklist
Create a standard checklist for vetting vendors:
- Administrative Safeguards: Do they have written security policies? Regular staff HIPAA training? Named security officer?
- Physical Safeguards: How do they secure their data centers or offices?
- Technical Safeguards: Do they encrypt data at rest and in transit? Use MFA for their internal access? Maintain audit logs?
- Prior Breaches: Have they had any security incidents or OCR investigations? Transparency here is good.
- Subcontractors: Will they further subcontract any PHI-related tasks?
- Breach Response: Ask how quickly they notify customers of an incident
- Data Return/Deletion: Upon contract termination, will they return or destroy PHI as required?
Document the answers and have your compliance/privacy officer review them too. This kind of due diligence isn't just best practice. If a vendor breaches PHI, OCR will ask if you performed due diligence in vendor selection.
Specialized Healthcare Cloud vs. General Cloud: Pros, Cons, and Key Differences
Should you use a healthcare-specific cloud provider (like MedStack, Aptible, ClearDATA, etc.) or stick with a general cloud (AWS, Azure, GCP) and configure it for HIPAA? This is a common dilemma.

Specialized healthcare cloud providers are appealing for small to mid-sized teams where speed to compliance is crucial and in-house cloud security expertise is limited.
General cloud platforms offer maximum flexibility and the backing of huge ecosystems.
Strategic Compliance Frameworks: Risk-Based Roadmaps, Audits, and Accountability
Checklist compliance is not enough. You need a strategy to continuously manage HIPAA risk. Forward-thinking CTOs are implementing frameworks that prioritize security investments based on risk, map out audit preparation, and assign clear responsibility to stakeholders.
Risk-Based Prioritization
Not all HIPAA controls carry equal weight for every organization. Perform an enterprise risk assessment (as required by 45 CFR §164.308) and use the results to prioritize remediation.
For example, if you discover that your new EMR integration with Epic is transferring PHI via an unencrypted interface, that's a high-risk finding to fix immediately. On the other hand, if you find a minor policy gap that doesn't pose real risk, that can be scheduled later.
Many of the largest fines have come under the "willful neglect" category, where organizations knew or should have known of a security weakness but did nothing.
Governance and Accountability
Covered entities must establish a governance structure for HIPAA compliance. At minimum, designate a Security Officer (required by HIPAA) and likely a Privacy Officer (required by the Privacy Rule). In a startup this might be the CTO or a senior engineer wearing the hat.
Create a responsibility matrix for key compliance areas using RACI (Responsible, Accountable, Consulted, Informed) methodology.
This prevents gaps where everyone thinks someone else is handling a control.
Audit Readiness and Simulation
Many CTOs dread the word "audit." But you can remove the fear by preparing methodically. Maintain an audit prep timeline:
90 days out
Do an internal compliance audit using the OCR Audit Protocol as a guide
60 days out
Compile key documentation: risk analysis reports, training attendance records, list of systems with ePHI, recent vulnerability scan results
30 days out
Conduct management briefings and audit interview prep
Even if no audit comes, this level of readiness ensures you're continually compliant.
Learning from Failures: HIPAA Audit Horror Stories and Consequences
What happens if you get HIPAA compliance wrong? In short: fines, corrective action plans, lawsuits, lost business, and leadership oustings. None of which you want to experience.
Multi-Million Dollar Fines
Large fines make headlines, and they are often tied to unaddressed systemic failures. Advocate Health Care Network was fined $5.5 million by OCR after a series of breaches affecting 4 million patients. OCR cited that Advocate failed to conduct an enterprise-wide risk analysis and lacked sufficient access controls and device protections.
Anthem paid a record $16 million settlement in 2018 for a breach of 79 million medical records; they had not adequately safeguarded a web portal.
The message: OCR will fine for egregious or neglectful non-compliance, especially if a breach exposed that negligence.
Business Impact and Valuation Hit
A less quantifiable but very real consequence is losing customer trust and business opportunities. When a breach is public, patients may leave en masse (remember that 70% of patients might switch providers after a breach).
In the private equity world, any hint of compliance problems will be factored into valuation (or can even derail a deal). PE firms have stated that cybersecurity issues can diminish an entire portfolio's value.
Operational Disruption
Beyond fines, imagine the internal chaos of failing an audit or facing a breach. Executives might be forced to resign (to show accountability). Your team will be diverted for months to remediation, documentation, and dealing with investigators.
For a stark example, think of LabMD, a lab that literally shut down following an FTC data security investigation. While that's an extreme case, it shows how fatal regulatory issues can become.
Real-World Implementation Timeline: 30/60/90-Day Compliance Plan
When faced with building HIPAA compliance from scratch (or remediating a mess), CTOs often ask, "How long will this take?" While it varies, you can accomplish a lot in a 90-day focused effort.
First 30 Days: "Foundation and Triage"
Week 1:
- Conduct a Risk Assessment (Day 1-10): Immediately perform a basic risk analysis of your systems handling PHI. Identify key assets (databases, servers, APIs), threats (hackers, employee mistakes), and vulnerabilities
- Designate Security/Privacy Officers: Assign who is responsible for HIPAA security and privacy compliance internally
- Kick off Policies and Procedures: Develop or adopt basic HIPAA policies using templates from reputable sources
Week 2-4:
- Quick Security Wins: Implement high-impact technical safeguards that are easy to do quickly
- Enable disk encryption on all servers and laptops
- Enforce MFA for all user accounts (especially VPNs, cloud consoles, and email)
- Install basic endpoint security on workstations
- Remove or disable any unnecessary services/users in systems
- Workforce Training (Day 15-30): Conduct an initial HIPAA training session for all employees. Document that this training happened
Days 31-60: "Build and Fortify"
Days 31-45:
- Close Remaining Gaps: Address medium-risk issues from your Month 1 risk assessment
- Set up audit logging on all applications and cloud resources
- Tighten network security groups or firewall rules
- Implement automatic timeouts/locks on systems
- Fix any Physical safeguard gaps
Days 31-50:
- Vendor Management: Inventory all third-party vendors and tools that touch PHI. For each, ensure a BAA is in place or initiate those agreements. Evaluate their security using your due diligence checklist
Days 45-60:
- Documentation and Governance: Expand your policy set into a more complete HIPAA Policy Manual. Finalize your Incident Response Plan and perhaps run an informal drill
- Security Enhancements: Deploy more robust security solutions as needed (WAF, SIEM, EDR, etc.). Ensure data backups are not only happening but also tested
Days 61-90: "Audit-Ready and Verify"
Day 60-75:
- Internal Audit and Gap Analysis: With most controls implemented, conduct an internal audit against the HIPAA Security Rule and your own policies. You can use the HHS Security Risk Assessment Tool
Day 75-85:
- Policy Finalization and Approval: Update all policies/procedures with any findings from the internal audit. Have leadership officially approve them. Distribute any new/revised policies to the workforce and collect acknowledgments
Day 90:
- Go/No-Go Check and Celebrate: At the 90-day mark, convene your team and review the compliance status. Ensure all critical items from the risk assessment have been addressed. Address any remaining "no-go" issues before you declare victory
This timeline is aggressive, but quite feasible for a small organization with focus. The key is to front-load the highest risks and foundational elements (risk assessment, policies, technical controls) and then iteratively improve.
Advanced Considerations for Complex Environments
Multi-Vendor Integration Compliance
Complex healthcare environments often involve multiple software vendors, each requiring individual HIPAA compliance verification. Integration points between systems create additional risk vectors requiring specific security controls and monitoring procedures.
Many of the largest healthcare breaches on record have originated at business associates. For example, the single biggest healthcare breach to date was a 2024 hacking incident at a claims processing vendor, exposing 190 million records.
Multi-vendor environments require:
- Comprehensive BAA management
- Consistent security standards across all vendors
- Integrated monitoring and logging systems
- Coordinated incident response procedures
Multi-Cloud Integration Compliance
Multi-cloud implementations require each cloud provider to maintain individual HIPAA compliance while ensuring secure data transfer and consistent security controls across platforms. You must verify HIPAA compliance for each cloud provider and implement additional security measures for cross-cloud data flows.
Regulatory Trend Analysis
Healthcare compliance requirements continue evolving with new regulations, updated guidance, and emerging security threats. The 2025 proposed updates to the HIPAA Security Rule are expected to remove the "addressable" implementation specification flexibility, essentially making all safeguards mandatory.
Current trends include:
- Increased focus on supply chain security
- Enhanced patient privacy rights
- Expanded breach notification requirements
- Integration of artificial intelligence governance
SOC 2 and HIPAA Integration
SOC 2 compliance often complements HIPAA requirements, particularly for technology service providers. You may need to demonstrate both SOC 2 and HIPAA compliance for comprehensive risk management and vendor relationship requirements.
SOC 2 Type II reports provide additional assurance for HIPAA compliance by demonstrating operational effectiveness of security controls over time. Align SOC 2 and HIPAA compliance efforts to maximize efficiency and reduce audit burden.
Final Takeaways
Here's the bottom line: strategic EMR HIPAA compliance isn't just about avoiding fines. It's about building competitive advantage. Organizations that get this right see reduced operational risk, improved vendor relationships, enhanced competitive positioning, and increased valuation potential.
The key to success? Move beyond checkbox compliance to implement risk-based frameworks that deliver real business value.
Focus on:
- Systematic implementation of high-priority requirements
- Strategic vendor selection
- Comprehensive audit preparation
- Ongoing compliance monitoring.
Your healthcare compliance program should position your organization for sustainable growth, successful audits, and optimal exit outcomes. Building this capability requires specialized healthcare technology expertise across your organization to execute complex compliance initiatives effectively.
The organizations that build robust, scalable compliance programs today will maintain competitive advantages as regulatory requirements become increasingly complex and enforcement becomes more stringent.
Remember, compliance is a journey, not a destination. The healthcare compliance landscape continues evolving, making strategic implementation more critical than ever. Don't just meet requirements. Exceed them in ways that drive business value.
CTOs' Top Questions on HIPAA Compliance
How long does EMR HIPAA compliance implementation actually take?
For most organizations, basic compliance can be achieved in 30 to 45 days with dedicated resources. However, comprehensive strategic compliance typically requires 60 to 90 days. Complex multi-vendor or multi-cloud environments may need 3 to 6 months for complete implementation. The key is starting with high-risk requirements and building systematically.
Do we need an official certification (like HITRUST) to prove HIPAA compliance?
No. There is no official HIPAA certification recognized by HHS. HIPAA compliance is demonstrated by your documentation and practices. That said, many companies pursue frameworks like HITRUST as a way to validate their controls. It's optional but can be a "gold star" for your security program.
What are the biggest vendor-related risks I should worry about?
The biggest risk is assuming your vendors are compliant without verification. Business associates cause many breaches, often by being the weak link in security. Have a standardized process. Pick vendors carefully, get a BAA, and do due diligence. Ask them about their security measures, breach history, and certifications.
Can we use multiple cloud providers and still be HIPAA compliant?
Yes, absolutely. Many organizations go multi-cloud for resilience or to use different capabilities. HIPAA doesn't prohibit multi-cloud or hybrid setups, as long as each environment is secured and covered by a BAA. You'll need BAAs with each cloud provider. The tricky part is ensuring consistent controls across clouds.
What about on-premises systems or legacy apps? Can they be made compliant?
Yes, on-prem systems can absolutely be HIPAA compliant. HIPAA is tech-neutral. The challenge is often that legacy or on-prem apps lack some security features by default. You might need to add compensating controls, like putting a legacy app behind a VPN and firewall if it can't encrypt its traffic.
Our company is small. Do we really need all this formal process? Will OCR even audit us?
It's true that OCR audits have historically focused on larger orgs, but small practices and startups are not immune. OCR has investigated breaches involving just a few hundred records when there were egregious violations. Moreover, if you're working with enterprise partners, they will likely require you to attest to HIPAA compliance.
How do we handle Dev/test environments with PHI?
Best practice is do not use live PHI in dev/test unless absolutely necessary. Use synthetic or de-identified data whenever possible. If you must use some real data, treat those environments as production-equivalent in security. Many breaches have occurred from non-production environments that were less secure.
What resources can we use to help with compliance?
There are several great resources you can leverage. HHS offers a Security Risk Assessment (SRA) Tool, a downloadable app that walks you through risk questions. The 405(d) HICP guidelines provide practical best practices for small, medium, large organizations. NIST's 800-66 guidance is essentially a HIPAA Security Rule implementation guide.
James founded Invene with a 20-year plan to build the world's leading partner for healthcare innovation. A Forbes Next 1000 honoree, James specializes in helping mid-market and enterprise healthcare companies build AI-driven solutions with measurable PnL impact. Under his leadership, Invene has worked with 20 of the Fortune 100, achieved 22 FDA clearances, and launched over 400 products for their clients. James is known for driving results at the intersection of technology, healthcare, and business.
Ready to Tackle Your Hardest Data and Product Challenges?
We can accelerate your goals and drive measurable results.

